How I Passed the PNPT: An In-Depth Review
On Feb 3rd, I was honored to have received the PNPT. It took several months of hard work to obtain the certification and I’m very proud. In this post, I’ll delve deep into my PNPT Journey, the resources I utilized and my advice for those who are looking to take the exam as well.
Where It All Started
I have a special place in my heart for TCM Security. They provided my first proper introduction to ethical hacking and network penetration testing in 2022. I remember when I first discovered the Practical Ethical Hacking course on YouTube. It’s an extensive course that covers the fundamentals starting with Linux, networking (OSI model, Three-Way Handshake), and Python and then segue-ways into all the fun stuff – the phases of a penetration test, complete with learning basic Linux and Windows privilege escalation in order to root a few capstone boxes.
The course also covers buffer overflow exploitation by crafting Python scripts in order to execute the attack against a Windows target. Then we get into web app pentesting by learning OWASP Top 10 and attacking OWASP Juice Shop, an intentionally vulnerable web application written in JavaScript. Finally, we get deep into the weeds of Active Directory pentesting by manually setting up our own vulnerable Windows Active Directory environment that consists of 2 Windows 10 machines as well as a Windows Server that will host the Domain Controller.
I took the main course a few times sporadically throughout 2023. Every time I was locked in and ready to pursue my PNPT dreams, life got in the way (such as landing my first security analyst role 😅). When I Saw that the PNPT was on sale during Black Friday in November, I was like let’s do it. So I did it.
Preparation
I spent the following 2 months going over the course again. I was deep in the Discord (shout out to Dewalt lol) asking for advice almost every week for help as I troubleshooted different attacks. I re-took all of my notes in Notion and made sure to organize the attacks by the phase of a pentest they would best be suited for.
Here is an example of the tree-like structure for my notes:
Notes
└───Active Directory
├───Initial Attack Vectors
│ ├───LLMNR Poisoning
│ ├───SMB Relay
│ ├───IPv6 DNS Takeover
└───Post-Compromise Enumeration
├───Bloodhound
├───Plumhound
I dedicated 3 hours or more a day while working as a Security Analyst by day. What always keeps me motivated to dedicate time to my studies and research is just my love of hacking. It’s the perfect field for those of us who are persistent and forever curious.
Exam
The PNPT is a hands-on 5 day external and internal penetration test that first requires you to conduct OSINT on the client in order to gather information and obtain initial access. From there, the internal penetration test involves enumeration and performing Active Directory attacks in hopes that you’ll obtain Domain Admin. It is a network penetration test, but the mindset applies to other forms of testing like web apps as well: you always need to enumerate your target, craft your plan of attack, and detect and report vulnerabilities.
After you’ve reached Domain Admin access, you must write a professional report detailing your findings, explaining each phase of the attack and provide remediation. Afterwards, you’ll be invited to perform a debrief where you meet with someone on the team to discuss your report and answer any questions they may have.
The recommended courses are as follows:
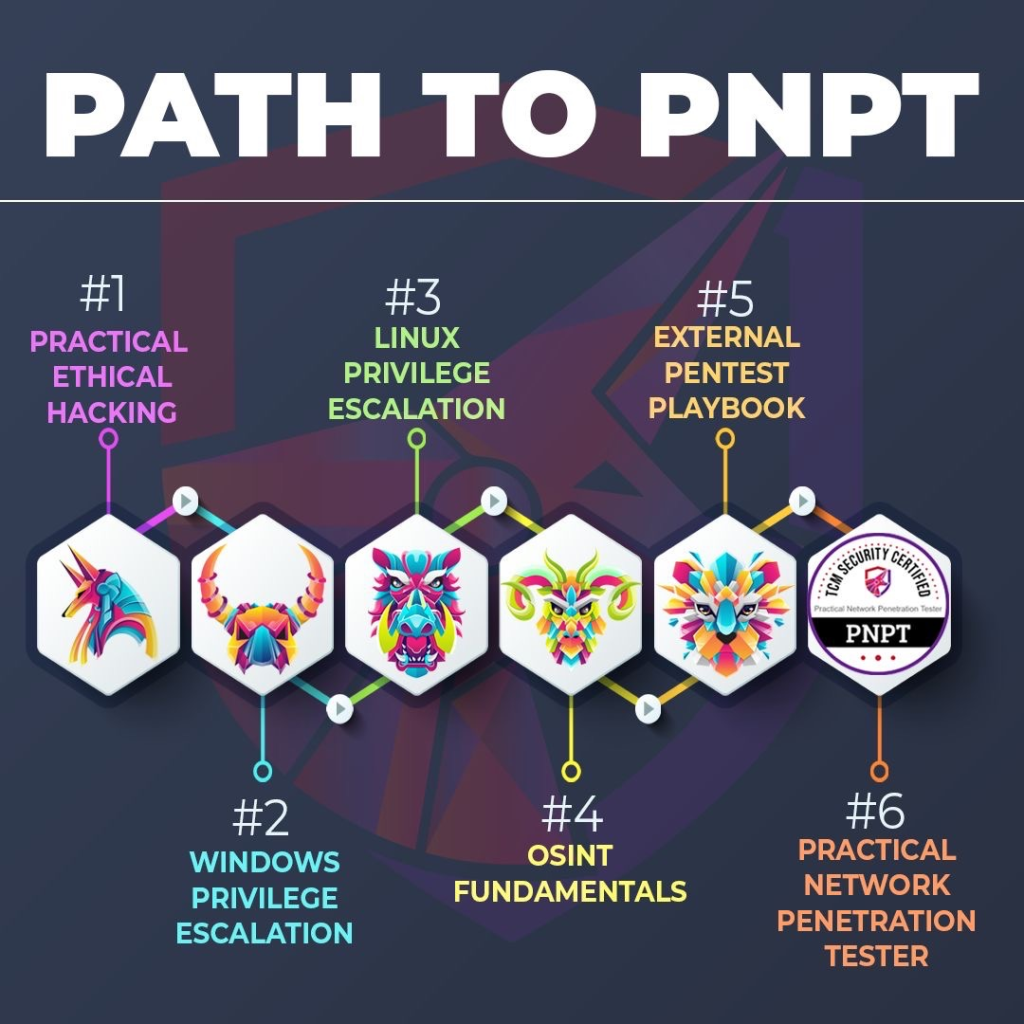
When you purchase the voucher for the exam, you’re provided lifetime access to all of the courses that are recommended.
My Thoughts on the Training
It’s A1. There’s a few things I enjoy about Heath’s style of teaching. To start with, I loved the Active Directory section because it not only shows you how to conduct the exploit, but you’re informed as to how these exploits work, what misconfigurations or built-in features need to be enabled in order for the attack to work and how to remediate. Remediation is key in pentesting because it’s not just about showing off your hacker skills but being able to demonstrate value to clients by educating on how to prevent these attacks from occurring again.
I became very acquainted with my favorite tool ever (after Burp Suite) which is crackmapexec (which is now NetExec), a tool where you can perform password spraying, perform pass the hash and pass the password attacks, and perform domain enumeration. There’s so much you can do with the tool that it deserves its own post really. Yes you learn how to obtain a shell with meterpreter but you also learn alternative ways to obtain a shell such as using psexec.
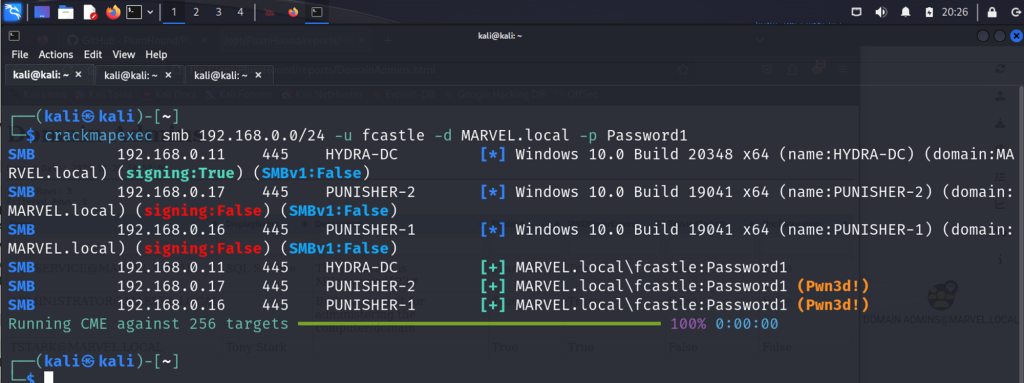
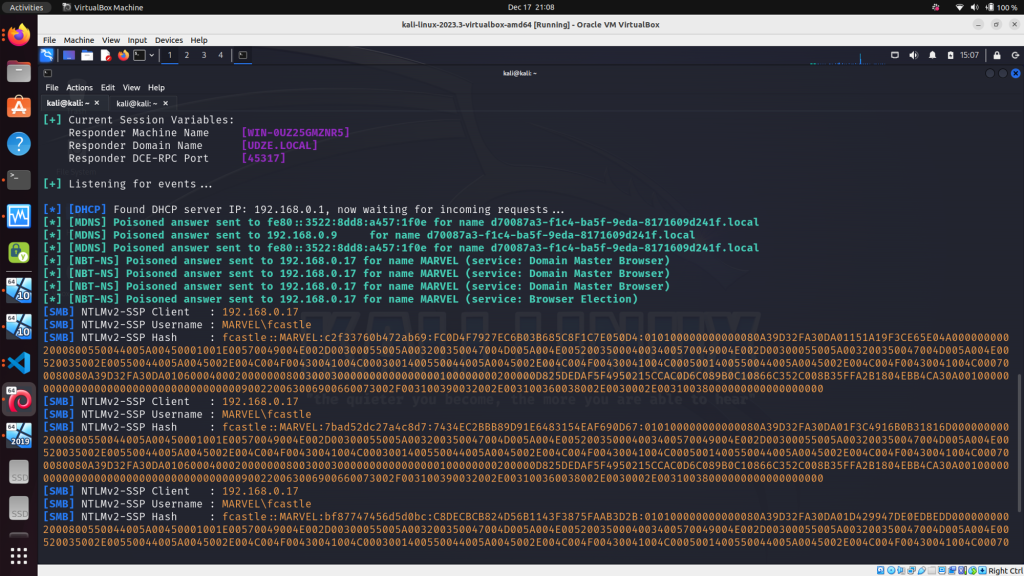
One of my favorite Active Directory attacks that I learned was using Impacket‘s Responder tool to perform LLMNR poisoning and capture NTLM hashes and using Hashcat to crack them offline. Another attack was performing kerberoasting attacks with Impacket again where you obtain the TGT hash of a service principal account (SPN) and depending on the privilege level of the account (such as domain admin), you can (hopefully) crack the hash and escalate privileges.
The OSINT Fundamentals course was really nice as well! This is a crucial course in the training because the very first step on the exam is to obtain information on the client by utilizing publicly available sources in order to begin your penetration test. You’re exposed to different tools but the takeaway is to learn how to find information manually, as from my experience, OSINT tools come and go.
The External Pentest Playbook course is fruitful for developing and refining your methodology when it comes to attacking a system from an external standpoint.
Finally, the Linux and Windows privilege escalation courses will be beneficial in your journey as you tackle CTFs or any boxes on Vulnhub, Hack The Box, TryHackMe or any other platform.
Resources
Outside of the recommended courses, I did TryHackMe’s Wreath room with the intended purpose of learning pivoting. This was based off of the many posts I saw on Reddit (I’m an avid lurker) where people recommended doing the room to pivot. However, I don’t think it’s necessary to do this and I didn’t realize that until I reflected back on my journey after passing. In the updated material, Heath goes over pivoting techniques with tools like sshuttle. I do still recommend doing the room because it’s a beautifully complex room where you a lot, including practical experience with pivoting.
Advice
- First and probably the most important, pay attention to Heath’s methodology. When you listen and take notes on how he tackles certain scenarios, you’ll notice a flow.
- If you’re running into ANY issue setting up your AD lab, do me a favor and download this. Dewalt, one of the employees at TCM, wrote a set of scripts that automates the setup of the whole Active Directory infrastructure in just a few clicks. This saved me!
- Make DETAILED notes. Write the steps of an attack like you were teaching to someone else. Make sure to explain the flags of a command so you don’t forget the purpose of them.
- Bookmark the TCM Discord – They provide round-the-clock support and help with any questions you may have. There is a dedicated PEH support channel for instance. Never be afraid to ask for help, the people there are some of the best examples of the good in the infosec community.
Overall Thoughts on the Exam
I would rate the exam as beginner to intermediate. I say it’s hitting intermediate level because you really do need to enumerate. Nothing particularly stands out like a CTF. I was stuck on OSINT for a few hours and reviewed my notes constantly and realized that there was something Heath said in the courses that helped immensely. Also, not once did I have to use Metasploit on the exam. I wouldn’t know how to compare the exam to the eJPT, OSCP or CPTS as I’ve yet to take those exams but I will say that the Active Directory attacks you learn in this training should prepare you for the AD portion of any of the exams. You’ll also leave the training with an improvement in your web and network pentesting methodologies, especially if you’re new to the game.
A big takeaway from this exam is that it’s not just about the tools, it’s more about your methodology. For instance, let’s say you obtain domain user credentials. What are your next steps? How would your plan differentiate when you’re enumerating from a credentialed standpoint as opposed to no user creds? Let’s consider another scenario. What if you discover an SMB share? What is your thought process on how you tackle enumerating that share? Do you try null session access? Having the persistence to constantly enumerate will take you far, not only in the exam, but just in general as a penetration tester.
My Future Goals
So, what’s next for me? I’m currently preparing for the Offensive Security Certified Professional (OSCP) exam. I’m also looking forward to tackling the PJWT, TCM Security’s web app pentesting exam as that’s my favorite domain when it comes to security, probably because of my web development background. I hope to keep producing meaningful content and taking you all along with me in my offensive security journey. I’m not just after certifications, I truly love to challenge myself and I think this is just another way of expressing my interest and effort in this field.
That’s All Folks
I hope you enjoyed my thoughts on the exam and the advice I had to offer. Please let me know when you decide to take it if you’re interested, I’d love to see how it goes for you. I highly recommend everyone who is interested in ethical hacking to start with the Practical Ethical Hacking course on YouTube (full course on their platform) and if you decide to pursue an exam, the PNPT is definitely a great place to start. Alright, bye!

Good info, thanks for sharing
No problem I’m glad you enjoyed 🙂
Congratulations Tae! This was very informative. Keep going…. I’m rooting for you!